If you want to learn how to hack someone’s Gmail account then you are on the right page. Here I will show you 5 different methods to hack a Gmail account.
On the internet, you can find websites/software clamming hack Gmail accounts within 5 minutes.
Gmail is a product of Google. Google is a billion-dollar company. Google pays a good amount of money if someone finds flaws in their system. Do you think these people will do it for free if they know how to hack Gmail?
The bottom line doesn’t waste your time. However, if there is no automated way it doesn’t mean you can’t hack a Gmail account.
You can do it using some technical knowledge and by making your users fooled. Keep reading to know how to hack a Gmail account in 2024.
Here are the working ways.
Phishing Attack
Phishing is the oldest method to hack accounts.
In the phishing method, hackers create a website that looks similar to the original Gmail website.
However when victims log in with their username & password. He will be redirected to the original site and you will receive login details. Check the following screenshot.
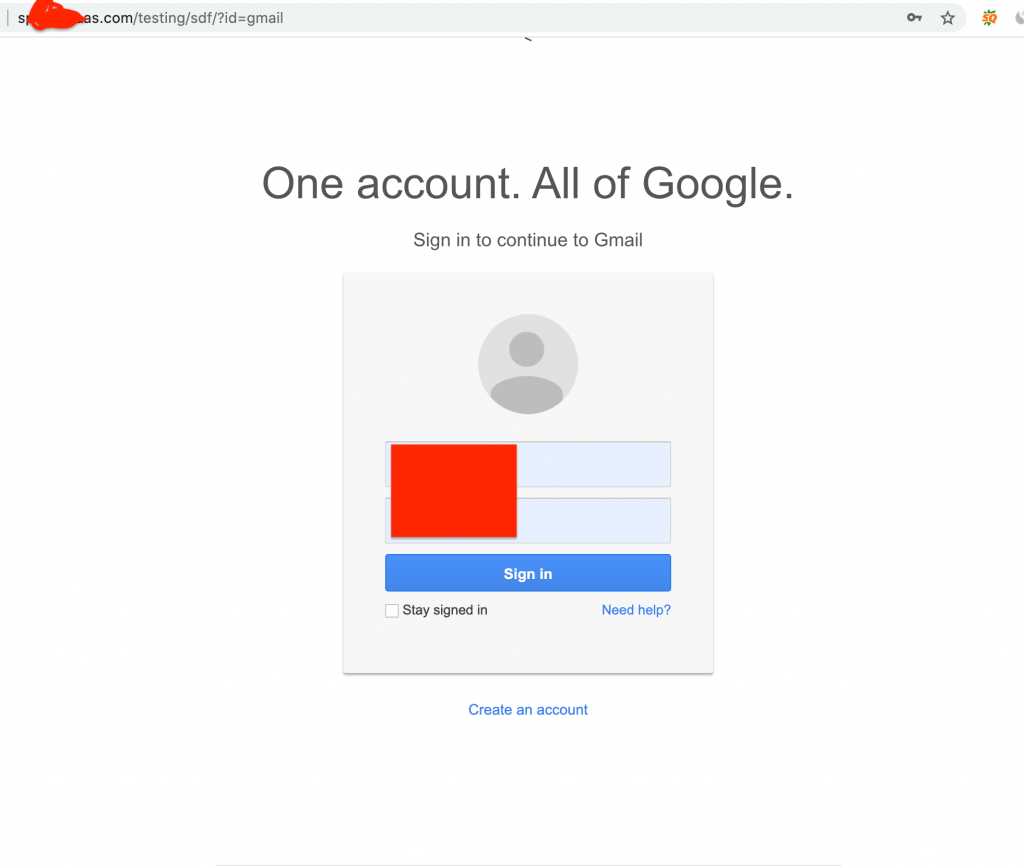
As you can see in the URL it is different than Gmail. You don’t need to learn to program. I will provide you script and free hosting that you can use to make your Gmail fake website.
How To Create Gmail Phishing Page
These days, the modern browser starts warning users when they visit phishing sites. However, I found the solution to this method. I made changes to the phishing script.
On another side, free hosting companies also start suspended accounts that use phishing scripts.
You can use paid hosting such as fastcomet, hostmaria, hostingspell.
The paid hosting companies also provide you with a 30-day money-back guarantee. Within 30 days, you can cancel your account and get the money back.
If you want to use free hosting then try 000webhost. Free hosting allows phishing for some time. They will suspend your account. If you are doing it for educational purposes you can use 000webhost.
You can download phishing script from here. I found half the working phishing script on GitHub and made a few changes to make it work.
For this tutorial, I will use free hosting, 000webhost.
I assume you know how to create an account for 000webhost. Just make sure you don’t install WordPress or don’t use any website builder.
We need to use a file manager for uploading the files. Here are the steps for uploading.
- Now login to your 000webhosting account. After that find the File Manager.
- Open it & go to public_html folder. Upload the phishing script that you downloaded. The following screenshot describes how to upload a zip folder
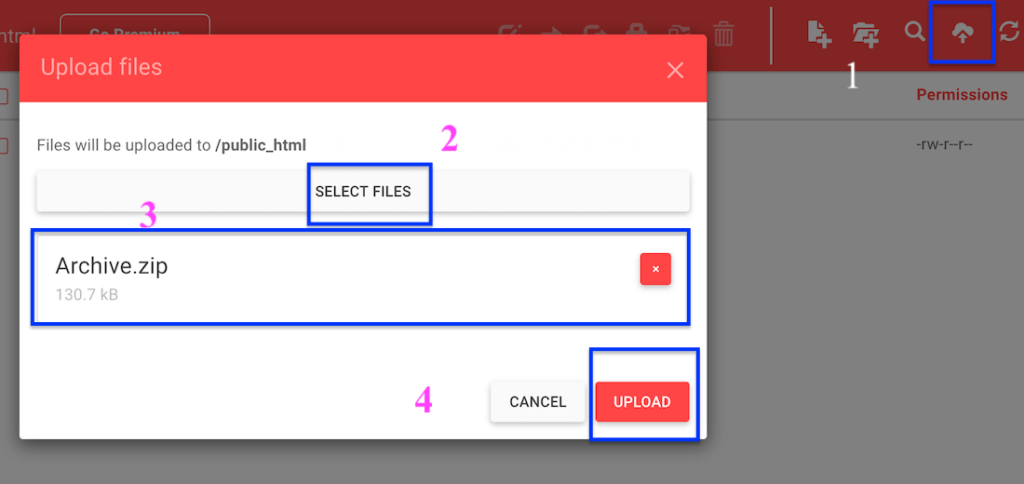
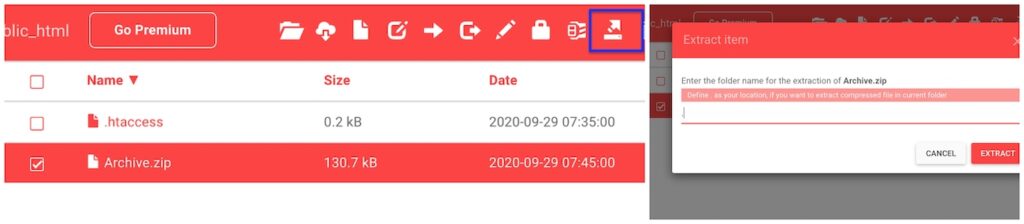
- After uploading, select the file and select the Extract icon. It will prompt you to the location. Type. (Dot). Sometimes 00webhost doesn’t allow you to extract files. You can extract phishing scripts on the device. Then upload all files at once.
There is no subfolder.
- Now Go back to My Sites, and open the site URL. It will show you something like this.

- Great you have done everything correctly. Now at the end of URL, just type ?id=gmail. It will open a page similar to the following page.

When the user login into the account his username & password will be saved in the users.txt file
You can access this file by typing yourwebsites..com/users.txt
Keylogger
Keylogger is another trending method to hack someone’s account. However, there is one big limitation to this method. You need to install software/apk on the user’s phone.
Basically, keylogger is a program that records every typed keyword through the keyboard. Thus when you victim login into your account it will also record the password.
In some cases, you don’t need a password. It will record everything such as messages etc that might be more interesting for you.
If you want to hack someone’s Gmail account then make sure you remove the account for the phone. Thus the user has to login back in again. When the user will log in back then his password will be recorded by the keylogger.
Keylogger software is available for computers and phones. You can also find apps in the play store. For computers, you can find keylogger software through the internet.
There are both free and paid keylogger apps available in the market.
The main difference between free and paid is paid keylogger will automatically send you data on your phone. You just need to install them once on the user’s phone.
On another side, a free keylogger can’t do it. You need to open the keylogger app again and again to view the data.
If you need a free keylogger then try a smart keylogger. It is 100% free. The beauty of a smart keylogger is it will divide data into parts depending on in which apps the user has opened the keyboard.
Thus it makes it easy when you look through the data and want to find something specific.
However, if you are looking for paid keylogger then try hoverwatch. It provides a free trial for 3 days with limited features.
Except for keystroke you will also get screenshots after every 5 minutes, contacts details, all call details, and device location as well.
Installing hoverwatch can be complex for non-techy human beings. Here is the step-by-step tutorial on how to install a hoverwatch on an android smartphone.
Man In Middle
I’m not going to show you step by step tutorial on how to hack someone’s account through man in a middle attack. Actually, I don’t know how to do it.
On the internet, all man-in-middle attacks is outdated. You can’t hack accounts using them. However, still this is a working method. That’s how hackers hack celebrities’ accounts.
Basically in the man in the middle, hack setup own network. All the user’s data that go through the network first to go on the hackers device and then to the network.
Thus hacker is the middle man, he can see all the data. If you really want to learn how to set up a man in the middle then you should have proper knowledge of networks and programming as well.
This isn’t something you can search on the internet and find a working method. You need to become hacker for this.
I thought I should include this so you know this is also a working method.
Social Engineering
Social engineering is basically using common sense. You can also use social engineering to fool so you can hack an account by keylogger or phishing.
A lot of people set a password using the name of dad/mom with a mixture of some other characters.
Some people use the same password for every account. So if you can get the password of another account then you might get their Instagram account.
How to Protect your account
Use a Strong Password. Here is my recipe to create a strong password. Think about a sentence in mind, anything. For this example let’s use the following one.
Tinku was Our First Dog.
Now Pick the first character of every word. It will look something like this
Twofd
Last but least add some special characters to it.
Two)(*fd
I have picked 098 special characters so I can remember. Now you have a strong password.
Password Recovery
This is by far the most famous method to hack Gmail accounts. I have hacked 100’s of accounts using this.
Probably you have also tried it before reading this article.
Basically when we click on the forgot password. Then by answering the simple question we can get the Gmail password.
Unlike other platforms, Gmail passwords can be recovered in more ways instead of just providing OTP.
If you can find a device that the user has used to log in account or a network that is used by your user to open Gmail then great you have passed the most difficult hurdle.
Google notes the IP address when we submit information. When our IP address is matching to the IP that is used to access Gmail in past it sends a signal to Google that it is a real user who wants to recover the password.
If you are a college student and want to hack your friend/girlfriend’s Gmail account who uses college wifi then make sure you are connected to college wifi while doing this.
Just type Gmail then click on the forgot password, then it will ask you for the last password. Click on the Try another way as shown in the screenshot.
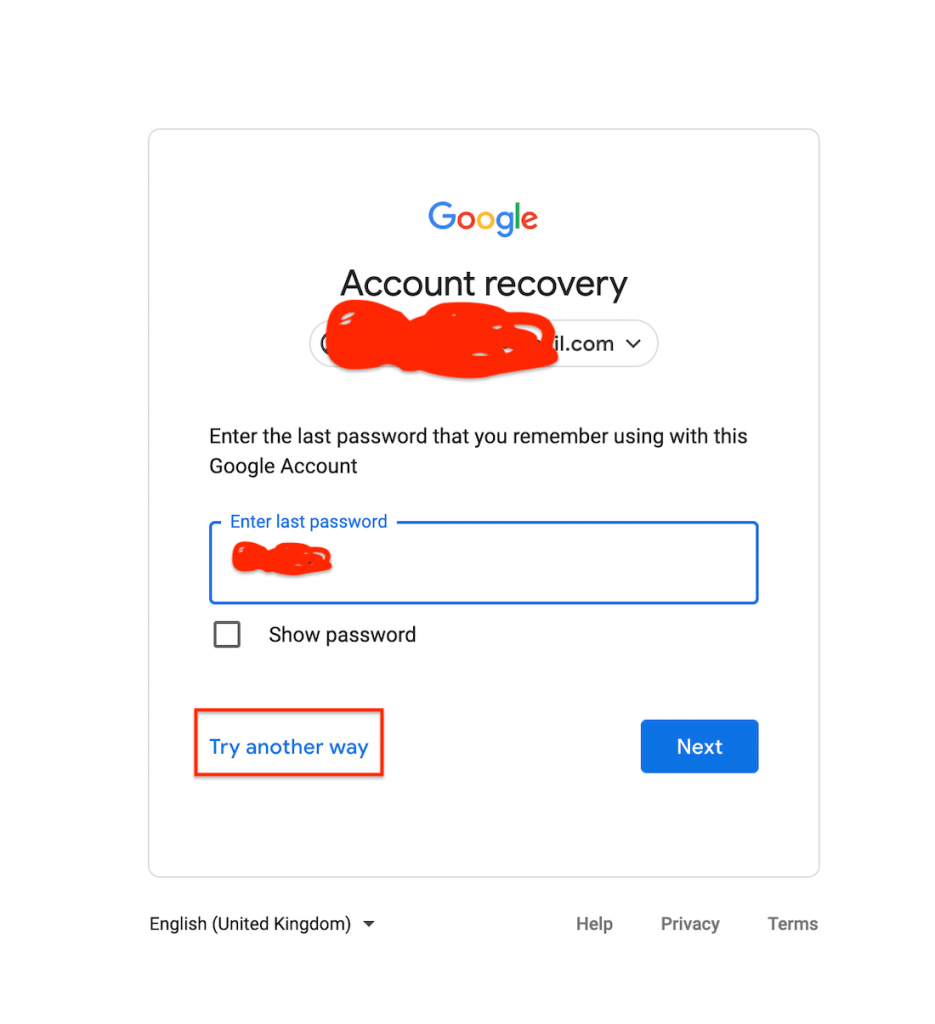
You may need to click on Try another way several times depending upon the security. It will even ask for the phone number again click on the I don’t have my phone.
Thus after this, it will ask you about an email address that we can use to contact you. Type your email then it will ask several questions such as the last time you have access to your Gmail account, and when did you make your Gmail account. etc
That’s where social engineering comes into play. You can get this question by asking questions to the victim when did you get your first phone?
Probably in the same month, your victim made a Gmail account. If you don’t become successful on the first attempt don’t worry try again.
How to protect yourself
- Use 2-step verification. Gmail needs 2-3 days to recover the account when some enable the step 2 verification. You will find out if someone is trying it hack your account.
Final Words
I hope you got value from this article. If you have any suggestions then let me know in the comment section. It may help other users.